Secure Azure Web Apps in private end point with Azure Application Gateways
I am providing the step-by-step instruction on how to Secure Azure Web Apps in private end point with Azure Application Gateways. One of the major use cases is, this is very much needed when the Azure virtual network is connected to the on-premises network and the organization need to access the web application privately through Azure Application Gateways.
The complete procedure is followed using azure PowerShell CLI to make it simple for those who are looking for some easy steps to achieve this requirement.
Let’s start with setting up some unique Variables for the entire PowerShell CLI session as below. You can set your convenient variable names.:
$rg="appgwPvtWebApp"
$planName="DemoPlan"
$appName="azureonlinedemoapp"
$vnetName="azureonlinedemonetwork"
$gwName="azureonlinedemogateway"
- Create a new Resource Group in your azure subscription.
az group create -n $rg -l "eastus" - Create a new App Service Plan. To be able to put a web app in a vNet using a private endpoint, the App Service Plan used has to be a Premium v2
az appservice plan create -g $rg -n $planName --sku P1V2 --is-linux - Create the .NET App
az webapp create -g $rg -p $planName -n $appName --runtime "DOTNET:6.0"
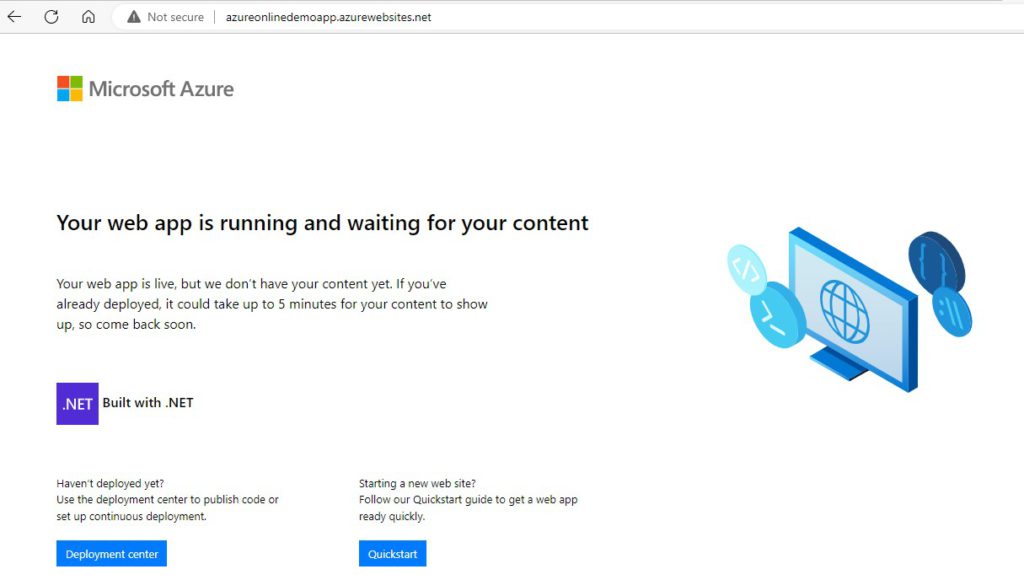
The Webapp should be accessible at http://azureonlinedemoapp.azurewebsites.net/
4. Create the vNet – Default VNet, App VNet
az network vnet create -n $vnetName -g $rg --address-prefix 10.0.0.0/16 --subnet-name Default --subnet-prefix 10.0.0.0/24
The network will use IP addresses between 10.0.0.0 and 10.0.255.255, and inside that network, the Default subnet will use the IP addresses between 10.0.0.0 and 10.0.0.255.
The Default subnet is where the Gateway will be created. We also need a subnet to be created for the application to be connected.
az network vnet subnet create -g $rg --vnet-name $vnetName -n Apps --address-prefixes 10.0.1.0/24
The IP addresses ranges from 10.0.1.0 to 10.0.1.255.
5. Create the Application Gateway and connect Default subnet with a public IP address
az network application-gateway create -g $rg -n $gwName --capacity 1 --sku Standard_v2 --vnet-name $vnetName --subnet Default --public-ip-address azureonlinePublicIp --priority 1000
Application Gateway connects the Public IP address using a “Frontend IP Configuration”. It then creates HTTP Listener called appGatewayHttpListener, which listen to port 80. It also creates appGatewayBackendHttpSettings, to forward calls to the backend target on port 80. A “backend pool” called appGatewayBackendPool is created to define the backend “targets”. A routing rule called rule1 ties all together by making sure that requests coming in to appGatewayHttpListener are redirected to the appGatewayBackendPool using the appGatewayBackendHttpSettings.
6. Configure the Gateway to redirect traffic to the application by adding the app to the appGatewayBackendPool backend pool with the following command
az network application-gateway address-pool update -g $rg -n appGatewayBackendPool --gateway-name $gwName --servers "${appName}.azurewebsites.net"
7. In-order to access the site by ip, we need to re-configure the HTTP Setting to use the host name from the target that we have defined in the backend pool as follows
az network application-gateway http-settings update -g $rg -n appGatewayBackendHttpSettings --gateway-name $gwName --host-name-from-backend-pool true
8. Set up the Private Endpoint. First, we need to disable the “private endpoint network policies” for the App subnet using a command as follows
az network vnet subnet update -g $rg --vnet-name $vnetName -n Apps --disable-private-endpoint-network-policies true
We can create the Private Endpoint and connect to the VNet using following two commands
webAppId=$(az webapp show -g $rg -n $appName --query "id" --out tsv)az network private-endpoint create -g $rg -n "${appName}-endpoint" --vnet-name $vnetName --subnet Apps --private-connection-resource-id $webAppId --connection-name "${appName}-connection" --group-id sites
Once a Private Endpoint is added to a Web App, it becomes “private” and public access from the internet is removed. However, through the Gateway IP address it will be accessible still. The solution is to set up a Private DNS Zone that allows the Gateway to route traffic to the application through the vNet.
9. Adding a private DNS Zoneaz network private-dns zone create -g $rg -n privatelink.azurewebsites.net
Linking to the vNet will allow DNS look ups inside the network. For that execute the following command
az network private-dns link vnet create -g $rg -n "${appName}-dnslink" --registration-enabled false --virtual-network $vnetName --zone-name privatelink.azurewebsites.net
10. Add the Web App to the DNS Zone by creating a DNS Zone Group for the Web App
az network private-endpoint dns-zone-group create -g $rg -n $appName --endpoint-name "${appName}-endpoint" --private-dns-zone privatelink.azurewebsites.net --zone-name privatelink.azurewebsites.net
11. The backend pool still tries to reach the Web App using the public address and thus need to “refresh” the backend pool by executing the following command
az network application-gateway address-pool update -g $rg -n appGatewayBackendPool --gateway-name $gwName --servers "${appName}.azurewebsites.net"
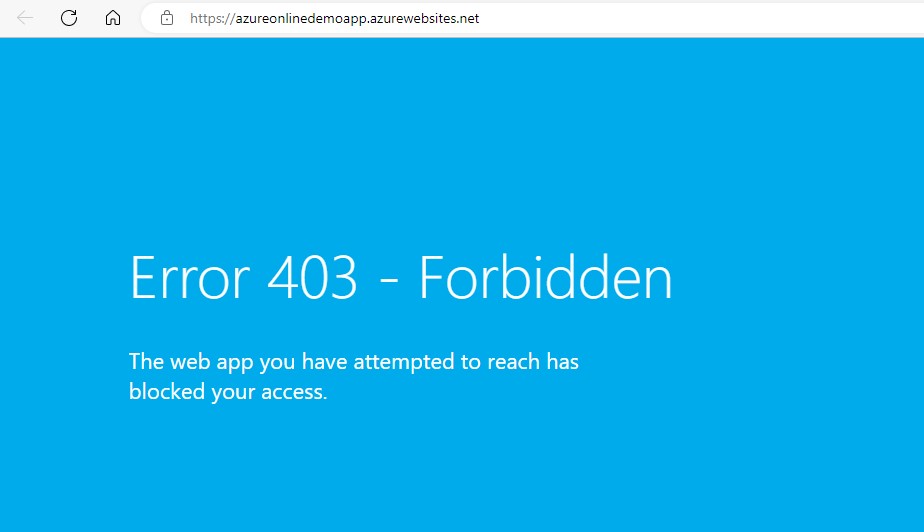
12. Following step changes the Access Restrictions by adding an Allow rule for the Default subnet, and a Deny rule for everything else. So, the Gateway, which is on the Default subnet is allowed to access the app, but resources on other subnets would not be allowed.
az webapp config access-restriction add -g $rg -n $appName --rule-name 'WebAppAccess' --priority 200 --action Allow --vnet-name $vnetName --subnet Default
Now, access to the application is limited to a subset of subnets. It throws the following error when try to access
13. Clean up
Cleanup is possible with a simple step as follows. This cleans up all the resources under the resouce group we created
az group delete -g $rg --yes

No responses yet