Assign RBAC permission to AAD groups with Logic app
Azure REST API can be used to create RBAC permission assignments to Azure Resource Groups from a Logic App as I am explaining below:
Create an Azure Logic APP, add a Workflow
Create Logic Design, Add HTTP Trigger
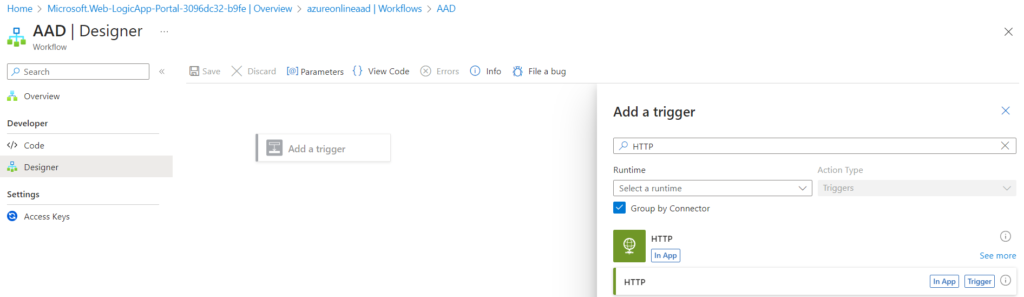
Add the HTTP Trigger. Now we need to find the values to be filled for the HTTP Trigger. First, we can go for finding the GUID of the role we are going to assign the AAD Group. For this, go to the subscription blade and select Access Control (IAM) as shown below. On the Details column, select the ‘view’ option corresponding to the role. I have selected ‘Contributor’ role in this example
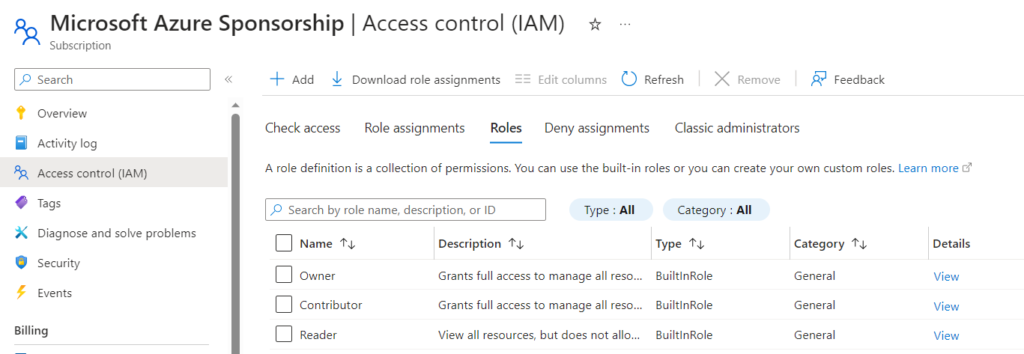
Select JSON tab to find the GUID of contributor role as indicated below:

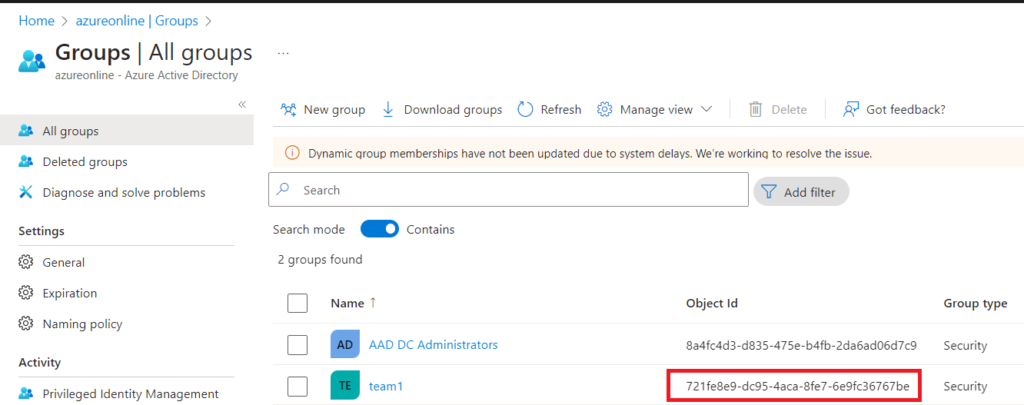
We also need to find the GUID of AAD Group. Select the group and find the GUID a below:
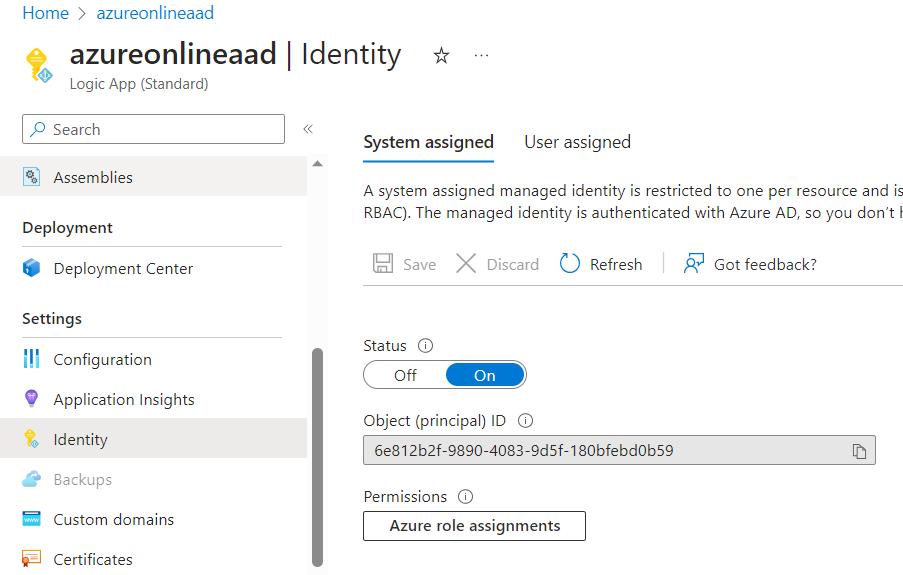
Now, we need to set certain parameters of the Logic App (You may need to open a different window). Go to the Settings > Identity and set the Status of System Assigned as ‘On’.
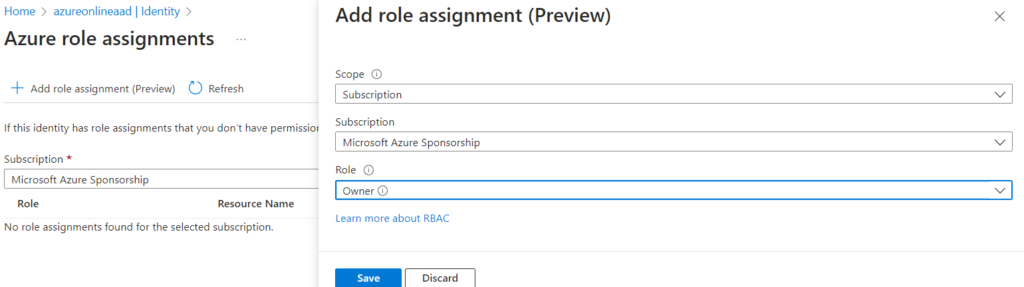
Assign the required permission by clicking ‘Azure role assignments’. I have assigned owner permission for this example purpose
Now we are ready to fill the values for the trigger we started creating. Fill the values as below:
URI:
https://management.azure.com/subscriptions/<Sub ID>/resourceGroups/<RG Name>/providers/Microsoft.Authorization/roleAssignments/<guid of contributor role>?api-version=2022-04-01BODY
{
"properties": {
"roleDefinitionId": "/subscriptions/<Sub ID>/resourceGroups/<RG Name>/providers/Microsoft.Authorization/roleDefinitions/<GUID of Contributor role>",
"principalId": "GUID of AAD object"
}
}Assign the Authentication details as below:
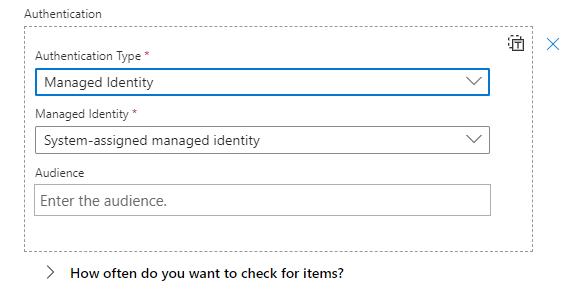
Finally, the HTTP Trigger will look like as follows: (Stroked out sensitive values)
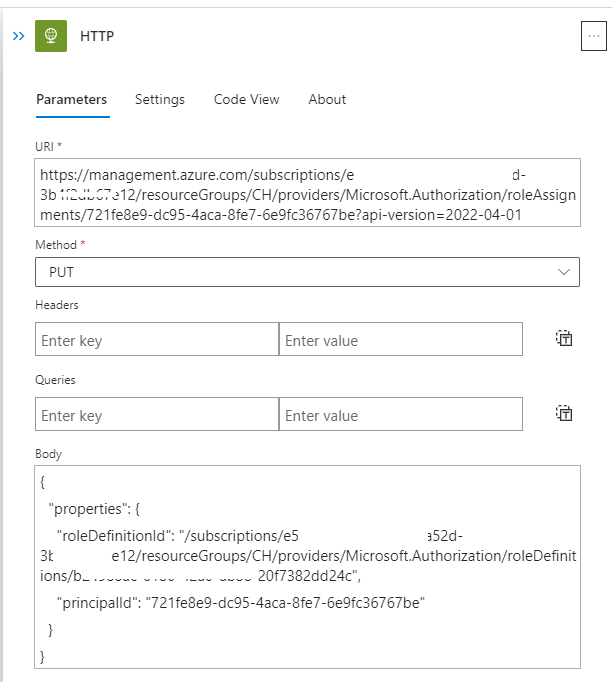
Save the HTTP trigger and we are ready to start a test run
Run Logic App and RBAC permission assignments to AAD Group
Run the Logic App from Overview section
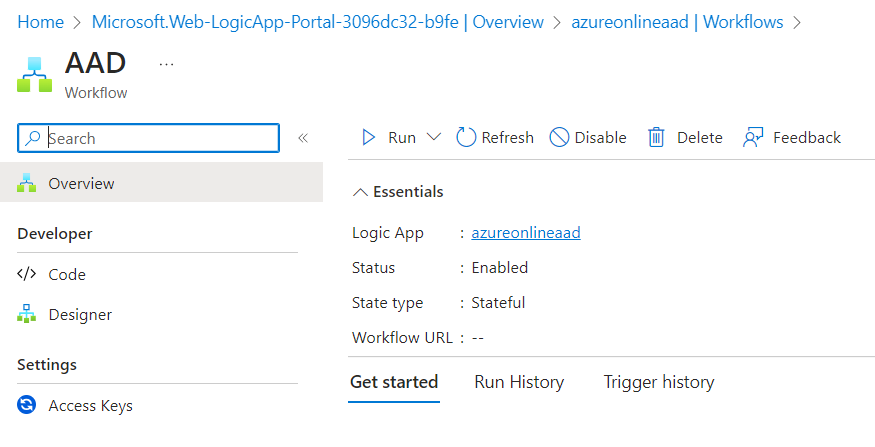
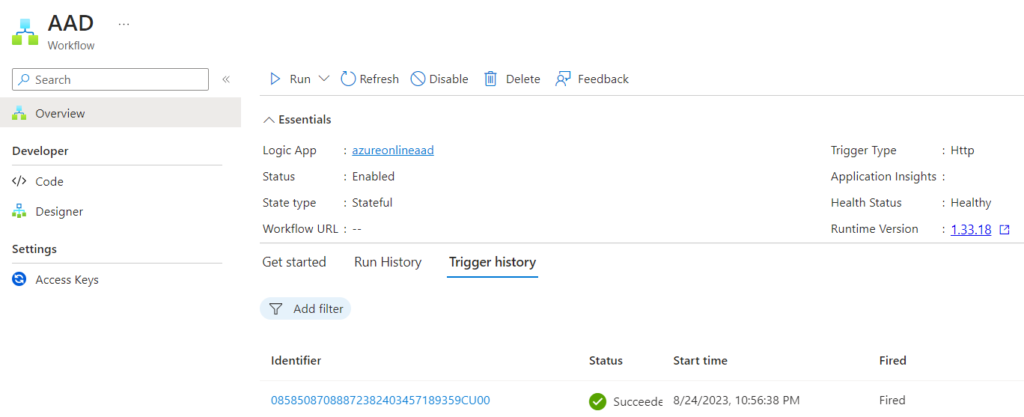
Verify Run History/ Trigger History and see the job has succeeded
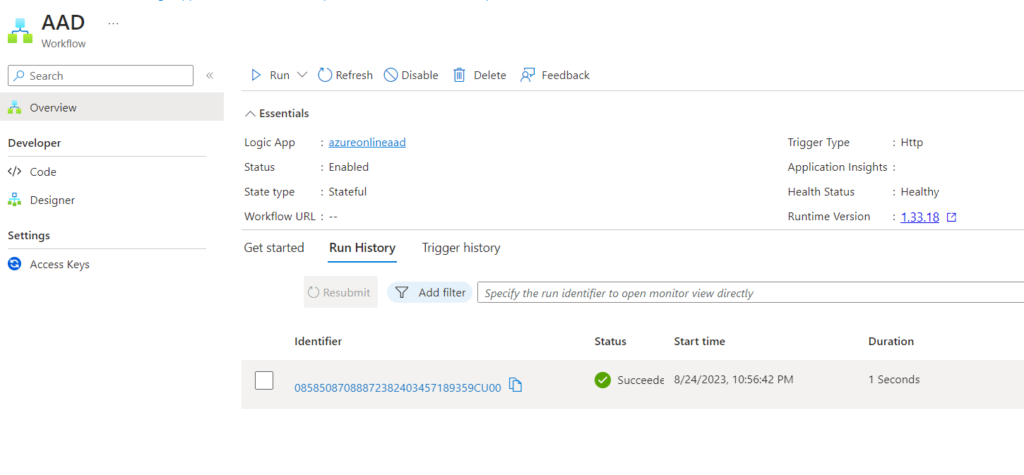
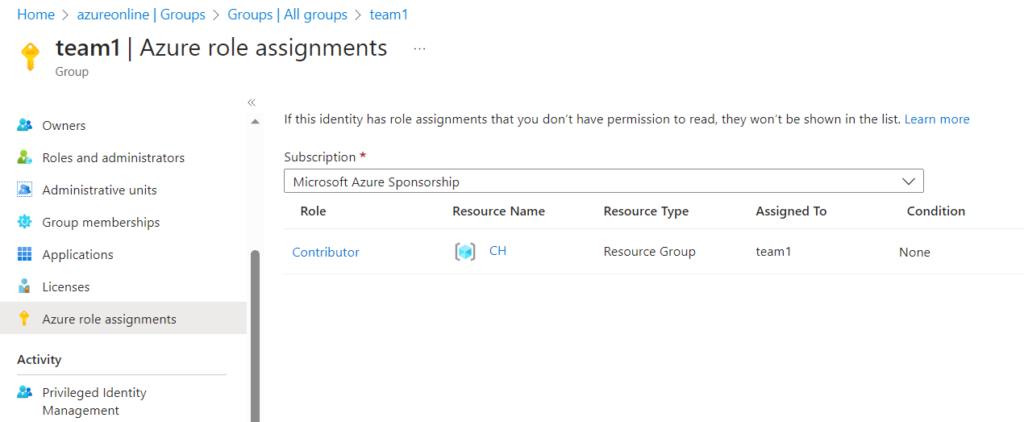
Finally, verify the AAD object to see that the ‘Contributor’ role assignment was successful

No responses yet